Despite the name, VPN concentrators are usually found in corporate settings where many devices and multiple networks are used to protect servers. What is a VPN Concentrator?
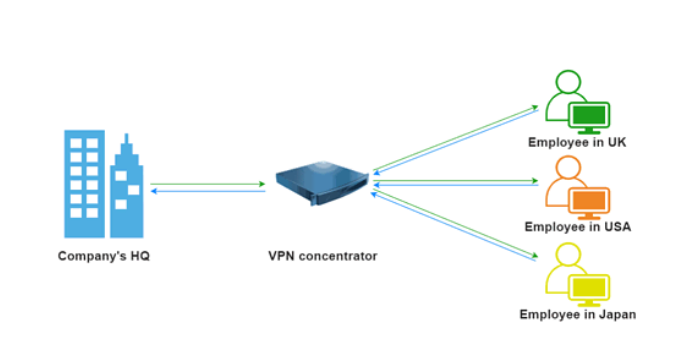
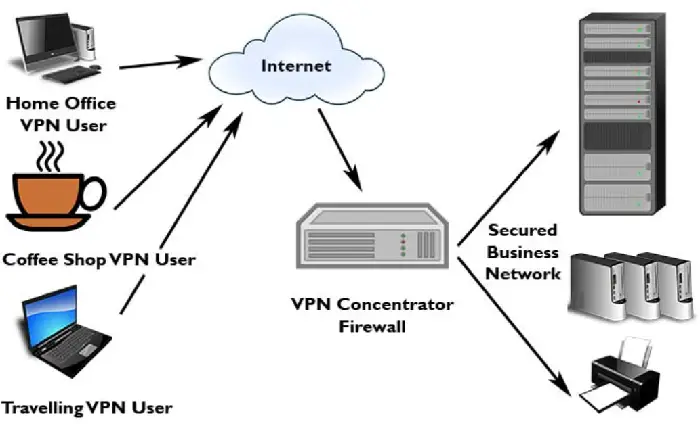
The VPN Concentrator is a networking device that enables numerous VPN tunnels to share a single network connection. VPN tunnels are secure connections that protect data from the Internet using modern encryption techniques.
Here, we present a complete guide on what a VPN concentrator is, how it works, and when and where to use it.
Buy: NordVPN
See Also: What Is Zlib1.Dll And How To Fix Zlib1.Dll Missing Error
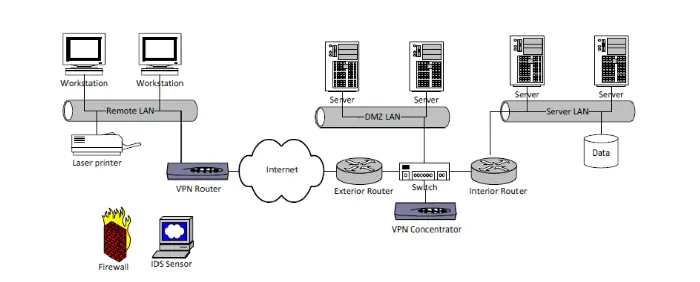
VPN Concentrator
A VPN Concentrator is a device that can establish secure connections across a TCP/IP network, such as the Internet. This feature allows users to develop certain private relationships across public networks without worrying about hackers intercepting their communications.
The VPN Concentrator is a networking device that enables numerous VPN tunnels to share a single network connection. VPN tunnels are secure connections that protect data from the Internet using modern encryption techniques.
Site-to-site VPN designs are often built using a VPN concentrator.
It may be able to:
- Construct and configure tunnels.
- Users are authenticated before tunnel/IP addresses are assigned to them.
- Data encryption and decryption
- Ensure that data is delivered from beginning to finish.
After reading so far, you may now know what a VPN concentrator is.
Who Makes Use Of A VPN Concentrator?
Businesses and organizations that run numerous systems networked together employ VPN concentrators. This connection could be made via a private network, such as a rented phone line, or a public network, such as the Internet.
VPNs will shield operators’ systems from any communication eavesdropping if they require their systems to be secure.
Remote individuals can safely connect to a network with the help of VPN concentrators. By installing VPN concentrators, they can also enable numerous users on a single device to connect to diverse users on a different network.
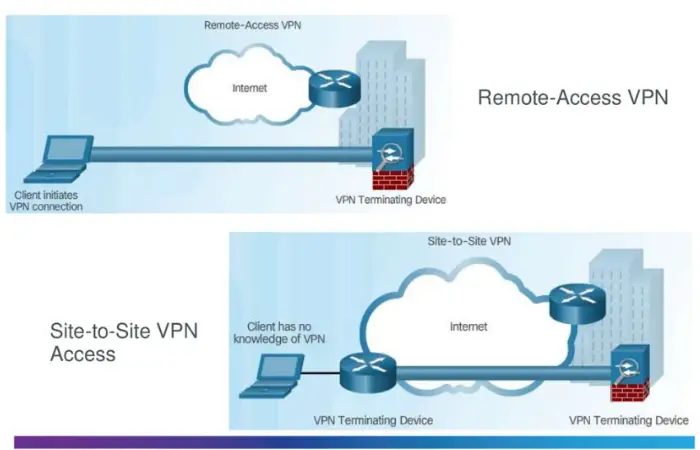
Site-To-Site VPN Vs. VPN Concentrator:
Concentrators are very different from site-to-site VPN connections. A site-to-site VPN is best if you link two or three locations.
This configuration is best for permanent locations, such as a home office or branch offices in different cities. The very same databases and systems are accessible through tunneling protocols.
The ideal choice, however, is a VPN concentrator if you want tunneling protocols to provide remote access from mobile devices, sporadic locations, or multiple users simultaneously.
See Also: Crypto.com Card Declined? This Is What You Can Do
IPsec Encryption Versus VPN Concentrator
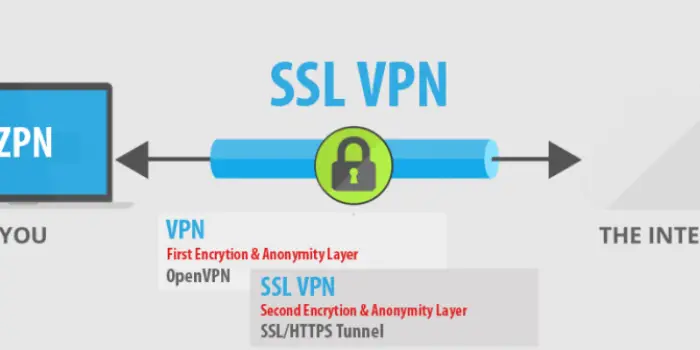
Internet Protocol Security (IPsec) or Secure Socket Layer (SSL) encryption technologies are typically used by VPN concentrators.
While most browsers also utilize SLL, the SSL VPN uses TCP port 443, which works best with most networks. The setup is alterable using port forwarding.
This stage permits using user credentials and installing SSL VPN clients into current browsers or operating systems. Because SSL VPN works on the browser and sends data back to the concentrator through the encrypted tunnel, you don’t require further IPsec tunneling.
It is unnecessary to manually configure each end-to-end device and client software when using SSL VPNs. However, some programs or software only permit IPsec VPN connections if you need to reach the OS remotely.
For users to access the VPN tunnel using IPsec, separate client software is necessary. It has more excellent local access and security configuration options than SSL-based VPN concentrators.
See Also: How To Fix Hulu Error Code 504
The Favored VPN Concentrators
Similar to virtual private networks, there are numerous VPN concentrator manufacturers. The range of VPN tunnels a concentrator can handle and its workload capacity affect how much it costs.
A few of the most popular brands are listed below:
- Cisco makes concentrators for VPNs. Their concentrators are generally easy to install and suitable for big organizations. A good illustration is Cisco Meraki.

- ShoreTel offers VPN servers to build a safe IP phone network. Installing remote IP telephony networks that safeguard IP phones is possible with ShoreTel’s VPN concentrators.
- Aruba and HP are the only companies to finish first and second in desktop/laptop and mobile markets. Additionally, HP is a leading supplier of VPN concentrators. Their tools help connect distant users to your corporate system. Also, click here if your VPN is slow.
How Does A VPN Concentrator Work?
VPN concentrators use tunneling protocols to construct and manage VPN tunnels. It accepts incoming data, encrypts, and de-encrypts it. It wraps incoming network data in encrypted packets and sends it across the VPN tunnel.
In addition to user authentication, a VPN Concentrator assigns IP addresses to each user. It also handles network interactions using standard protocols and manages cryptographic keys.
The “man-in-the-middle” attacks use VPN concentrators and routers to listen in on connections to a target company’s network.
You’ve probably been told often not to connect to your workplace network through public Wi-Fi. Because publicly accessible routers may not even require passwords to connect, cyber attackers can quickly sniff login credentials or intercept emails.
Why Use VPN Concentrators?
VPN concentrators deliver high-performance output, are efficient and productive, and may be scaled up utilizing Scalable Encryption Processing (SEP) modules. These allow consumers to boost overall capacity and performance even further.
VPN concentrators can accommodate tens of thousands of users. With remote-access users connected to the VPN network, VPN concentrators can function at the core of a small organization. They’re also necessary for businesses and organizations, as they can easily handle more than 10,000 users. Also, read this article for Avast VPN Problems.
See Also: 5 Ways To Fix Windows 10 Activation Error 0x8007007b
VPN Concentrator VS. VPN Routers
Both devices do the same thing, yet they differ in many ways. A concentrator can manage thousands of VPN clients, resulting in excellent business environments where employees may securely connect to private networks from anywhere.
On the other hand, VPN concentrators are unsuitable for home use. Buying and installing a device is not a good investment unless you live in a top-level government or private workplace with many corporate secret data.
Our small businesses and homes can use routers to connect to private networks. VPN routers are less expensive than concentrators, yet they often have the same functions as concentrators, such as USB connections, Ethernet ports, wireless connectivity, etc.
So far, you know what a VPN concentrator is and how it works. Let us see its encryption protocol types.
See Also: 3 Ways To Fix Netflix NW-2-5 Error Code
VPN Concentrator Encryption Protocol Types
A VPN concentrator employs at least two encryption protocols to protect communications, discussed in greater depth below.
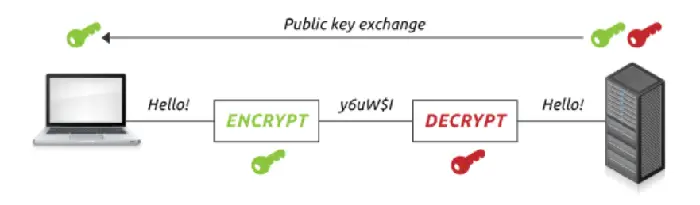
Encryption Using IPsec
Most VPN concentrators employ Internet Protocol Security (IPsec) to protect connections. Although the protocol is incredibly safe and effective, it necessitates installing VPN connection software on all devices in a business.
It’s best for a corporation with a headquarters and multiple branch offices.
Encryption With SSL
Another alternative is to use Secure Socket Layer (SSL) encryption. This protocol uses the Transmission Control Protocol (TCP) Port 443. It does not necessitate the installation and configuration of software on users’ computers or devices.
It also allows them to connect to their business network from any location; however, they can only connect to web-based applications.
See Also: 5 Ways To Fix Reddit Error 503 | Quick Fixes
Key Benefits Of Using VPN Concentrators
Users having internet connections from anywhere globally may safely connect to the company network. The VPN Concentrator reroutes and reshapes its network traffic.
Over an encrypted tunnel, the encryption procedure transfers the data and requests to the business server after completing the encryption process. When a communications request is generated, the VPN tunnel usually is created instantaneously.
When you first run the program, it will immediately construct a tunnel to the VPN concentrator, allowing you to receive any data via it.
We can set software programs to be Always-On, which means that whenever you turn on your device, it will connect to the corporate network via the VPN concentrator over an encrypted tunnel.
Hackers can hack a company’s network to plant malware or steal confidential data. In these commercial contexts, VPN concentrators provide security and encryption.
Using a remote desktop program can be helpful for home users, especially if you have a changing IP, but it is not appropriate for company servers.
At the absolute least, they should have a VPN router connected to the network. Because manufacturers no longer produce standalone concentrators, this term has become synonymous with VPN concentrators.
They include the features of multifunctional routers that also have a firewall. A VPN concentrator acts as a specialized router.
See Also: Top 4+ Cybersecurity Standards You Should Know About in 2024
FAQs
Is VPN Concentrator a router?
Yes, VPN concentrators are routers. However, not the ones you use at home. These concentrators are used explicitly for integrating multiple VPN networks.
What are the disadvantages of using a VPN?
As good as it looks, using VPN has its disadvantages as well. Lack of granular security, unreliability, degraded performance are some of the drawbacks we face while using a VPN.
What are the types of VPN networks?
Although there are numerous VPN networks available, three major types of VPN prevail worldwide: IPsec tunnels, Dynamic MultiPoint VPN, MPLS-based L3VPN.
Conclusion
There are various options for securing your networks with dependable encryption and protecting them from external threats. One of the most complex security network solutions available is the VPN concentrator, which is only one of the options.
While prominent vendors’ VPN concentrators support SSL and IPsec VPNs, lower-cost equipment often only supports one of these protocols.
Some applications are incompatible with SSL-VPN clients. Furthermore, specific SSL-VPN systems may not allow centralized storage or shared access to resources like printers. Your unique needs will determine the procedure you should employ.
IPsec VPNs are the most secure and give higher security than SSL-based VPNs. In addition, the SSL-VPN concentrator will be easier to set up and administer, lowering the possibility of security flaws due to misconfiguration.
We hope to answer your questions about a VPN concentrator and how to use it. Also, click here to fix Err_SSL_Version_Or_Cipher_Mismatch Error.
See Also: How To Solve VPN Error Code 51 On Windows PC

Matt Brown: Senior editor with expertise in consumer tech, gaming, Xbox, and Windows PCs. Follow him on Twitter @mattjbrown for the latest updates.